Please note that for this we need to have access to your server using SSH protocol, so you need to have your SSH credentials at hand.
If your website is using WordPress (or other CMS) is where our scanner shines the most, because it applies firewall rules that are specific to those platforms and frameworks.
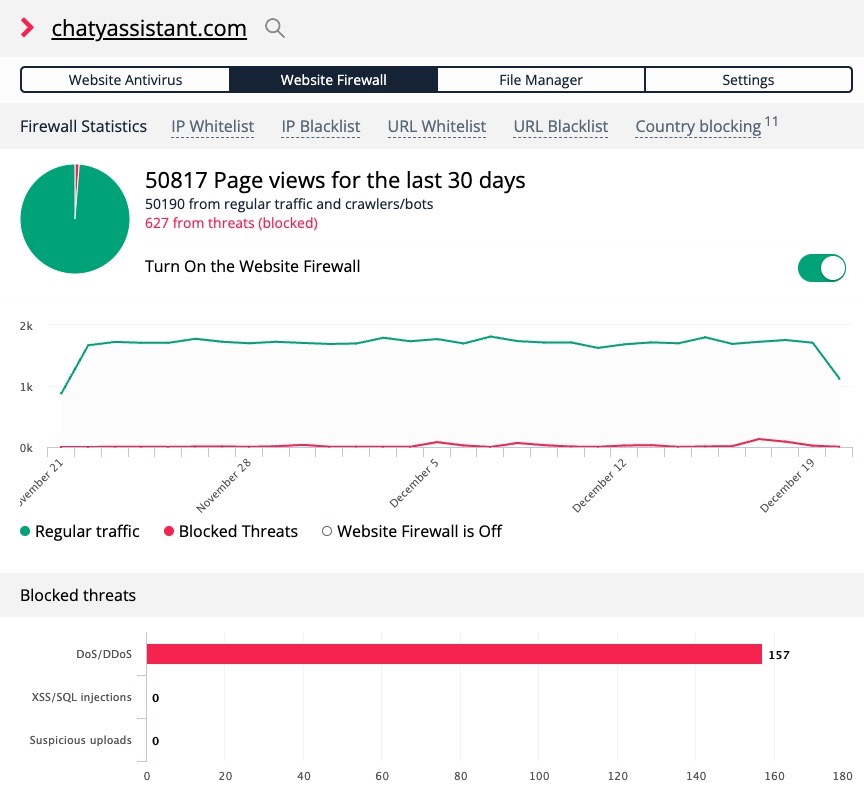
The firewall works automatically as soon as our file is installed in your server. It loads before your website and serves as a shield. It receives every request to your website. The website firewall is connected to our anti-malware servers, which analyze requests as they are received.
Example:
Please note that firewall rules are specific to:
Joomla, Wordpress, DLE, Drupal 6.x/7.x/8.x/9.x, ModX Evolution/Revolution, 1C Bitrix, Yii framework 2.x, OpenCart, CS.cart, NetCat, PrestaShop, HostCms, UMI.CMS, Amiro.CMS, Magento, CMS Made Simple, XenForo forum, CodeIgniter, PhpBB, Webasyst, Stressweb, DiafanCMS, Vtiger CRM, Koobi CMS, Simpla, VipBox(Engio), InstantCMS, Symfony.
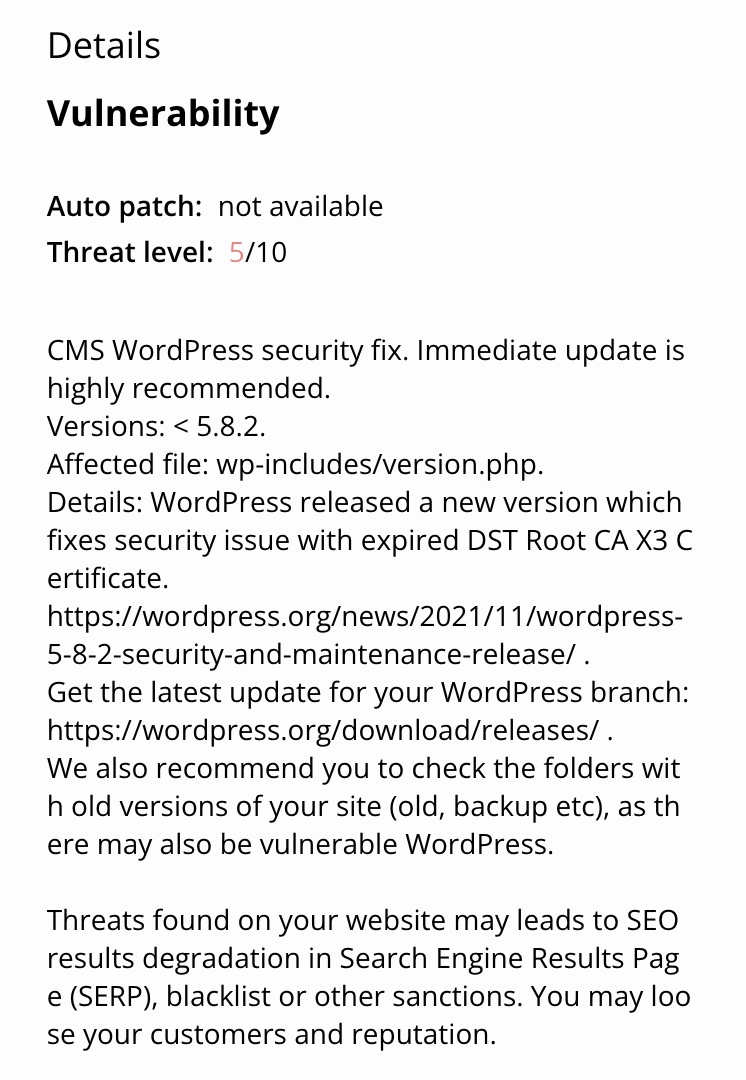
Our anti-malware network also collects and sends several alerts (specific to WordPress), detailing any vulnerabilities detected in the network, so we can take actions.
For example: